Passwordless Authentication is a method for authenticating users in a service without requiring a password.
Instead, the user may be authorised by an alternative factor such as a registered device, biometrics, or in the case of Single Sign-On systems, the user is already authenticated by a third party. In this case, a token is then passed to the service to allow the user access without being required to enter a password. We’ll take a look at how passwordless authentication works, as well as the technology and protocols used to implement it.
We’ll also look at why many enterprises are embracing passwordless solutions, the security challenges faced by the proliferation of cloud apps, and how they can be overcome.
How does passwordless authentication work?
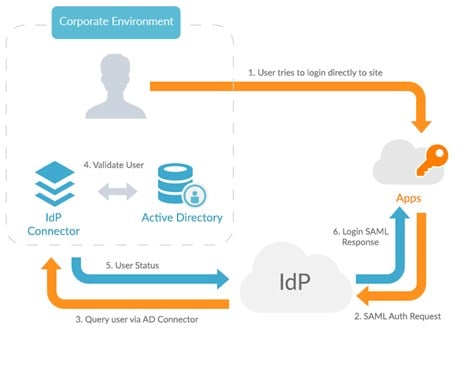
Passwordless authentication operates with a three-way relationship between three parties:
- The user – an individual wishing to access a service such as a cloud app
- A Service Provider (SP) – the service the user is requesting to access
- An Identity Provider (IdP) – a third party which authenticates the user
Instead of the normal procedure of the user entering their credentials directly into the SP’s app, the user is instead verified by the IdP, which then confirms the user’s identity via a protocol to the SP. This result is much more secure, as well as being quicker and easier for the user.
Identity Providers (IdPs)
IdPs are third-party systems which authenticate users in order to allow them access to applications without the use of a password. The IdP can authenticate the user in a variety of different ways, one such method is to integrate with the existing corporate directory (e.g. Active Directory), enabling the user to be automatically authenticated with the IdP once on the corporate directory.
The IdP effectively has the process of authenticating users outsourced to it by the apps the user wishes to access. This one identity is used across multiple apps, forming a federated identity that permits Single Sign-On.
The Passwordless Login Process
The end result of the three-way communication between user, IdP and SP is a simple process:
- A user identifies themselves to the Identity Provider, which authenticates them by use of a password, physical device, biometrics or some other means.
- The user then requests access to a service provider, such as by launching a cloud app.
- The IdP provides a security token to the service provider via the web browser.
- The service provider authorises the user, permitting them appropriate access for their identity.
While this process can sound complex, the actual user experience is far simpler and smoother than a password-based system. From the perspective of an employee at an enterprise using a passwordless system, they are simply able to launch and close apps at will, without having to enter their credentials after they are on the Active Directory.
SAML, OIDC and OAuth
In order to securely communicate with one another, the three parties will use an identity protocol to exchange the data. By far the most common of these are SAML and OIDC, the latter of which is built from the OAuth protocol. While the process is the same for both protocols, there are some key differences between them.
What is SAML?
SAML is one of the most common protocols used in passwordless authentication, and allows the user, IdP and SP to communicate securely. A SAML assertion is transmitted in XML from the IdP to the SP to verify the user’s identity and allow them access to the service. SAML also supports IdP-initiated sign-in, where instead of initiating the process by launching the SP app, the user first launches the IdP portal, and gains access to the app from there.
What is OIDC?
Similar to SAML, OIDC is a common protocol used for passwordless authentication. OIDC is an authentication layer which is built on top of the OAuth framework. The process is mostly the same as SAML, but there are some key differences. The user data, which is transmitted in JSON format rather than XML, is known as a claim, while the SP is instead referred to as the ‘Relying Party’ (RP).
What is OAuth?
OAuth is an open standard for authorisation, most commonly used to grant federated access between different websites and cloud apps. Access tokens are issued to third-party apps to allow a federated identity, where one user can access multiple services from the same identity.
What makes passwordless authentication more secure?
Why passwords cause businesses problems
The primary reason that enterprises move to passwordless solutions is that they are much more secure. Every password provides a potential point of attack for hacking and phishing, and the simple elimination of them greatly reduces the possibility of a data breach.
Data breaches cost businesses an average of £2.71m per breach in 2020, resulting from lost business, reputational damage, system downtime and a loss of new and existing customers. Worse, the trend has been steadily increasing year-on-year, both in average cost and in the number of breaches. In addition, the average time to detect and contain a data breach came in at a worrying 280 days.
Hackers frequently focus on passwords as an attack vector - 80% of hacking-related data breaches are caused by weak, reused or otherwise compromised passwords. Phishing is a particular source of concern, with 90% of compromised passwords involving some kind of phishing or social engineering. Despite growing awareness to the threat, over 50% of employees still click on phishing links.
Why passwordless authentication prevents malicious attacks
The secure-by-design nature of passwordless authentication means that many of the techniques used in malicious attacks are rendered ineffective.
Brute force attacks
This involves simply forcing through as many random guesses as possible at a rapid rate. Without a password, this technique can’t be used.
Credential stuffing
Similarly to brute force, this method attempts lots of guesses, but using a vast database of previously compromised combinations of usernames and passwords. Again, with no password, this is not an option for malicious attackers.
Keyloggers
Malware which can record keystrokes entered to discover username and password combinations. With a SAML or OIDC token replacing usernames and passwords, the identity of the user cannot be compromised.
Shoulder surfing
The simple act of physically looking at a person entering a password can still pose a serious security risk. Passwordless authentication removes this threat when signing onto a cloud app involves simply clicking through to the app.
Phishing
A user is contacted, usually by email, and directed to a fake website where they would normally input their credentials. Since in a passwordless Single Sign-On System the user does not enter a password, and does not know the password even if there is one, employees cannot compromise the system and allow a data breach.
Social engineering
This involves a variety of techniques where a password is predicted from a user’s public data, or the user is convinced to reveal the password themselves. Even in cases where a SP is not compatible with security protocols such as SAML, some IdPs can still provide a passwordless experience of Single Sign-On where the password is randomly generated and unknown to the user, meaning this method is also ineffective.
Finally, there are additional benefits besides security for enterprises. Filling out credentials takes time, and so does resetting them when things go wrong. According to Gartner, 20-50% of all helpdesk calls are for password resets, with each one costing an average of £50. The wasted hours and resources quickly add up, leading to thousands of lost hours of productivity each year for larger businesses.
5 Reasons businesses move to passwordless solutions
1. Increasing security of systems and data
By far the biggest benefit of passwordless authentication for enterprises is to mitigate against data breaches. As we’ve seen, many techniques used in malicious attacks are ineffective in a system with a passwordless solution. By removing one of the biggest attack vectors, the possibilities of suffering a data breach are reduced enormously.
2. Keeping control over authorisation - shadow IT
Integrating a passwordless, Single Sign-On system has the added benefit of helping businesses keep track of which apps are being used. The number of actual apps in use has been shown to be up to 20 times higher than CIO estimates, leading to further security risks which are not immediately apparent to IT departments and CIO/CISOs. By being able to keep track of these apps and add or remove them from the passwordless system, enterprises gain much more control over their systems.
3. Easier to respond to breaches
A significant reason why data breaches can become so costly is the time taken to identify and respond to them – an average of 280 days, according to an IBM report. With a passwordless, Single Sign-On system, it becomes much easier to track unusual behaviour and to manage the access of employees centrally.
4. Time saved for employees
The time spent entering, changing and resetting passwords adds up for large enterprises, with 73% of companies saying their employees spend over one hour per day navigating between apps. As well as providing a much smoother user experience, a passwordless system also increases efficiency in the workforce.
5. Time/resources saved for IT
IT departments spend enormous amounts of time on password resets, with the majority of helpdesk calls being solely related to this issue. With a passwordless authentication solution in place that eliminates the problem of forgotten passwords, organisations save on the time and money used to manage password resets.
Implementing passwordless authentication
Use of IdPs
Businesses wishing to implement passwordless authentication for applications will first need an IdP to handle the management and authentication of users. Access Management (IAM) and Identity as a Service (IdaaS) providers fulfil this IdP function.
How IdPs create passwordless solutions
An IdP will authenticate all users in the directory to any third-party apps they wish to use, through a passwordless, Single Sign-On solution. To choose the best IdP, businesses will have to consider which of their most commonly used apps are compatible with Single Sign-On protocols, such as SAML and OIDC. If apps are not compatible, some IdPs may offer workaround solutions which still provide a passwordless experience.
Moving to passwordless future
When moving to a passwordless system, existing users can be migrated by uploading metadata to compatible SPs, while each app will have to be configured to accept SAML/OIDC requests. For new users, many IdPs provide ‘Just-in-time provisioning’, where the user is registered as a new account automatically as soon as they click to access the service.
How My1Login enables organisations to implement passwordless authentication
My1Login act as the IdP to provide passwordless authentication for enterprises through its access management and Single Sign-On solution. As well as comprehensive integration with cloud apps, My1Login also provides Single Sign-On for legacy Windows desktop apps.
My1Login’s passwordless authentication solution does not require the organisation to change their existing directory (e.g. Active Directory). Instead, My1Login compliments this, integrating with the existing corporate directory to provide a seamless experience for users. The user simply authenticates with their corporate directory and My1Login delivers seamless authentication into all application types.
My1Login utilises SAML and OIDC to replace passwords with token-based authentication, enabling organisations to move away from passwords and to passwordless authentication. Where the SP does not yet support passwordless authentication protocols, My1Login’s Secure Web Authentication can be used to provide a passwordless experience, even for applications which have non-standard login pages.
My1Login leverages token-based authentication where available by the service provider, and where not yet available, performs Secure Web Authentication to remove the need for end-users to know, manage or enter application passwords. On an organisational level My1Login eliminates the most common sources of data breaches, while on the user level, a smoother working experience increases both efficiency and productivity.












