
Why Zero Knowledge Encryption is a critical consideration for an Identity Management Solution
Identity and Access Management (IAM) and Identity as a Service (IDaaS) vendors typically store some of the most sensitive corporate data on behalf of their customers – employee login credentials which are stored to enable Single Sign-On (SSO) for enterprise applications that protect an abundance of corporate data. As a result, a secure encryption process is paramount to protect enterprise data from being misused or compromised in a data breach should the identity management vendor be the victim of a cyberattack.
Most vendors will use various forms, or even combinations, of AES and RSA encryption, two highly secure algorithms for encrypting data to ensure it is unusable without access to the corresponding decryption key. However, the location where this encryption takes place and where the keys are stored is a critical security consideration so here’s what you need to know.
Encryption at rest
Any remotely credible vendor in this space will talk about how your data is encrypted at rest – simply put your credentials are encrypted before being stored. That means the encryption must take place at some point upstream in the data transit process. There are typically two ways to encrypt passwords upstream:
- Server-side in the IAM/IDaaS vendor’s cloud
- Client-side within the secure perimeter of the customer’s enterprise network
Instinctively you might think client-side is more secure and, to an extent, that’s true. However, there is a very important subtlety to be aware of and that relates to who has access to the encryption keys. In some implementations of client-side encryption the vendor can have access to your encryption key and simply ship it down the wire to your client device where it is used to encrypt your data. Technically this encryption happens “client-side” but it has all the vulnerabilities of service-side in that the IAM or IDaaS vendor has access to your keys and therefore your data. Here’s a bit more on each of these encryption architectures:-
Server-side encryption
For server-side encryption, the IAM vendor will receive the raw data (i.e. your employee’s usernames and passwords for cloud apps) from the client (i.e. your employee’s browser) and encrypt these in their own environment before storing them. This means your data is at risk in transit and once it reaches it’s destination because the IAM vendor has access to the keys that decrypt your data. Hence creating a significant additional risk factor should the vendor be breached in some way.
Server-side encryption is deployed by many IAM providers as it significantly reduces overheads and development complexity for the vendor. Vendors known to employ server-side encryption are also more likely to be targeted by cyberattacks, given the great value to cybercriminals of being able to access data and decryption keys in the same location. Fundamentally, server-side encryption increases the attack surface for enterprise customers as the IAM provider holds everything necessary to decrypt customer data.
Client-Side with keys known to vendor
Some vendors are known to provide client-side encryption but with insecure architectures that the vendor ships the encryption key to your employee’s browser in the same session that they shipped the encrypted passwords so they can say they use client-side. Unfortunately, this means that the vendor still has access to the encryption keys and data that protect customer’s data and the data is still at risk in transit since the encryption keys themselves are being shipped over the same wires as the encrypted data.
This can help these vendors create a powerful marketing message and tick the client-side box but it is does little to mitigate the risks of server-side encryption.
Client-side with keys unknown to vendor (Zero Knowledge Encryption)
In contrast, Zero Knowledge Encryption means that encryption will only be carried out using keys that are held by the customer, before the data is shipped up the wire to the IAM vendor’s cloud. As a result, the data will be encrypted before being sent and the vendor will have no means of decrypting the data. Should the vendor suffer a data breach, attackers will only gain access to the encrypted data which is useless without the keys to decrypt it.
While some vendors may promote server-side encryption as eliminating the overheads and risk of managing and storing encryption keys, Zero-Knowledge Encryption actually incurs no additional costs and requires no specific technical knowledge on the part of the customer – it simply means that the vendor has no access to the keys. True Zero Knowledge encryption is only achieved when the vendor lacks any ability to decrypt the customer data.
The benefits of zero-knowledge encryption
IAM/IDaaS Vendor cannot decrypt data
The primary benefit of Zero Knowledge Encryption is that the Identity Management vendor has no ability to decrypt any customer data sent to them or stored in their cloud. The data cannot be searched and interrogated by the vendor, mitigating the risk of it becoming compromised by a malicious actor internal to the vendor.
Vendor does not represent an attack vector
Vendors deploying server-side encryption, while offering cybersecurity services to their clients, actually increase the potential attack vector for their customers when compared to Zero Knowledge Encryption. As well as a potential attack occurring directly against the client, their data and decryption keys could be compromised by an external attack on the vendor, over whose security policies they have no direct control. With Zero Knowledge Encryption, attackers would not be able to decrypt the data by breaching the vendor.
Data is encrypted when in transit
Since the data is encrypted before it is sent to the vendor to be stored in their datacentre, there is far less risk posed by a man-in-the-middle attack. Man-in-the-middle attacks occur when an attacker inserts themselves between two communicating parties, relaying the information to each of them to ensure they believe they are in direct communication. While this can occur when data is sent to the vendor unencrypted or is sent alongside the encryption keys, with Zero Knowledge Encryption, any attacker would gain access to the data, but not the key to decrypt it.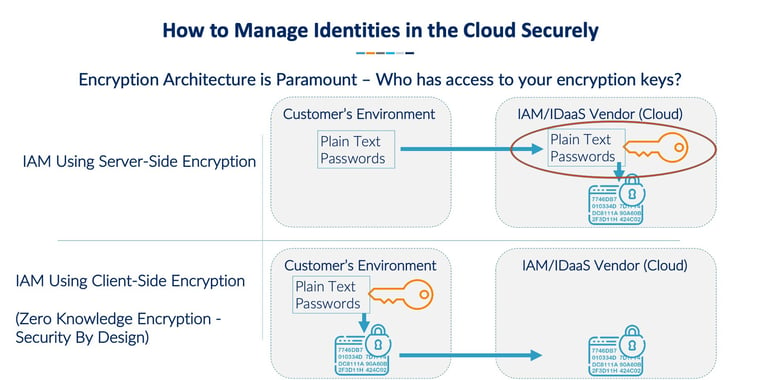
When choosing an IAM or IDaaS solution, any organisation will have to be assured that their data will be safe. Yet as well as the method of encryption used, the location where it is encrypted and the question of who has access to the keys are just as important. By choosing a vendor that uses Zero Knowledge Encryption, enterprises can be confident of reducing their attack surface by ensuring that, when it comes to storing employee login credentials for cloud apps, the encryption keys are stored segregated from the data.
So, the question you should be asking your potential vendor when undertaking due diligence is where is the data encrypted and who has access to the keys?
Learn more about the essential features to look out for when deciding which enterprise password manager is right for your organisation.
Related Articles
My1Login Approved as UK Government Supplier on G-Cloud 13 Framework
We are delighted to announce that My1Login has been approved as a G-Cloud 13 supplier – the UK Government procurement framework for public-sector bodies.The G-Cloud...My1Login named Winner at the 2021 Cloud Excellence Awards
My1Login is delighted to announce that it has been named the Cloud Security Product of the Year for Identity, Access and Authentication at the 2021 Cloud...Identity and Access Management for Web, Mobile and Windows Desktop Applications
Identity and Access Management for Web, Mobile and Windows Desktop Applications










-
© My1Login 2007 - 2026
- Terms & Conditions
- Anti-Slavery Policy
- Back to the top ↑
