The UK Public Sector and Local Authority Risks, Challenges and Mitigation Report provides an overview of the key risks and challenges faced by UK public sector and local council organisations. It summarises the source of the organisational risks, the consequences of these, and provides an outline of how many of these can be addressed.
The UK Government’s “Future Issues for Public Service Leaders” research and analysis published on the 25th July 2022 highlighted the key risks identified by public sector and local authorities as part of their corporate risk management processes. Using the outputs from this report, together with key risks identified by public sector and local authorities, we look at the source and consequences of the organisational risks, the typical Risk Controls cited, and how implementing the right Identity Management Solution can enable organisations to implement an extensive range of the necessary controls required to mitigate the risks.
Sector Pressures
The UK Government’s “Future Issues for Public Service Leaders” report highlights the following pressures facing the public sector:
| Finance and Funding |
| Delivering more with less |
| Workforce |
| Management retention and training |
| Political Landscape |
| Central Government policy shifts and constraints |
| Organisational Culture Change |
| Combating silos and short-termism |
| Covid 19 Response |
| The delivery change |
| Governance |
| Supervision of normal procedure |
| Customer Needs |
| How are these changing? |
Finance and Funding: Delivering More with Less
Finance and funding have long been concerns for leaders, particularly in sectors such as social care, local government, and further education. Public service leaders have long dealt with pressures to maintain or improve service delivery with current budgets.
Workforce: Management Retention and Training
Medium and long-term issues relating to the recruitment, management, training and retention of staff also feature strongly in the literature regarding current issues facing leaders.
Political Landscape: Central Government Policy Shifts and Constraints
The political landscape leaders operate in was the third-biggest group of concerns for leaders reported in the Government Skills and Curriculum Unit’s (GSCUs) year 2 baseline survey. The COVID-19 pandemic and EU Exit, and general political instability are recent examples of events which have challenged established norms in how policy is made. Although, we are seeing these challenges bringing greater focus on the need for developing contingency strategies.
Organisational Culture Change: Combating Silos and Short-termism
Issues around organisational culture were highlighted as an important issue for public service leaders by the GSCU teams and by the leaders themselves. Factors including issues of short-termism and “silo” mentalities in the public sector also featured in the literature.
COVID-19 Response: The Delivery Challenge
The COVID-19 response for leaders has been reported to be in large part a delivery problem. A key consideration at the start of the pandemic was how to operate essential services (including any additional services as a direct response to COVID-19) while shifting rapidly to new modes of working or management. This included the rapid shift of services online, establishing the necessary infrastructure for working from home, or in COVID-secure workplaces, and adopting ‘control and command’ structures for decision-making.
Governance: Suspensions of Normal Procedure
The evidence from the Institute for Government (IfG) analysis review described how the emergency response to COVID-19 resulted in the suspension or reduction of normal governance processes in many areas of the public sector to enable swifter decision-making. For example, the King’s Fund found that an immediate impact was reduced governance generally led to less risk-aversion and more innovation, facilitating rapid collaboration among public services, and between the public, private and voluntary sectors.
Customer Needs: How are These Changing?
The changing needs of service users were not considered to be one of the key issues by public service leaders directly. However, understanding and anticipating how public attitudes and expectations change was agreed to be an important area of interest by the GSCU. The challenge being building public trust, aligning services to the public’s priorities, and how to encourage increased engagement from the public in service design and delivery.
Satisfaction with services is currently static or improving slightly – two thirds were satisfied with their local council in February 2021, slightly above pre-pandemic levels, while 2020 GP Patient Survey data showed satisfaction above 80%, as it had been in 2018 and 2019. It remains to be seen if these scores can be sustained as the country moves into recovery.
Key Pressures by Sector
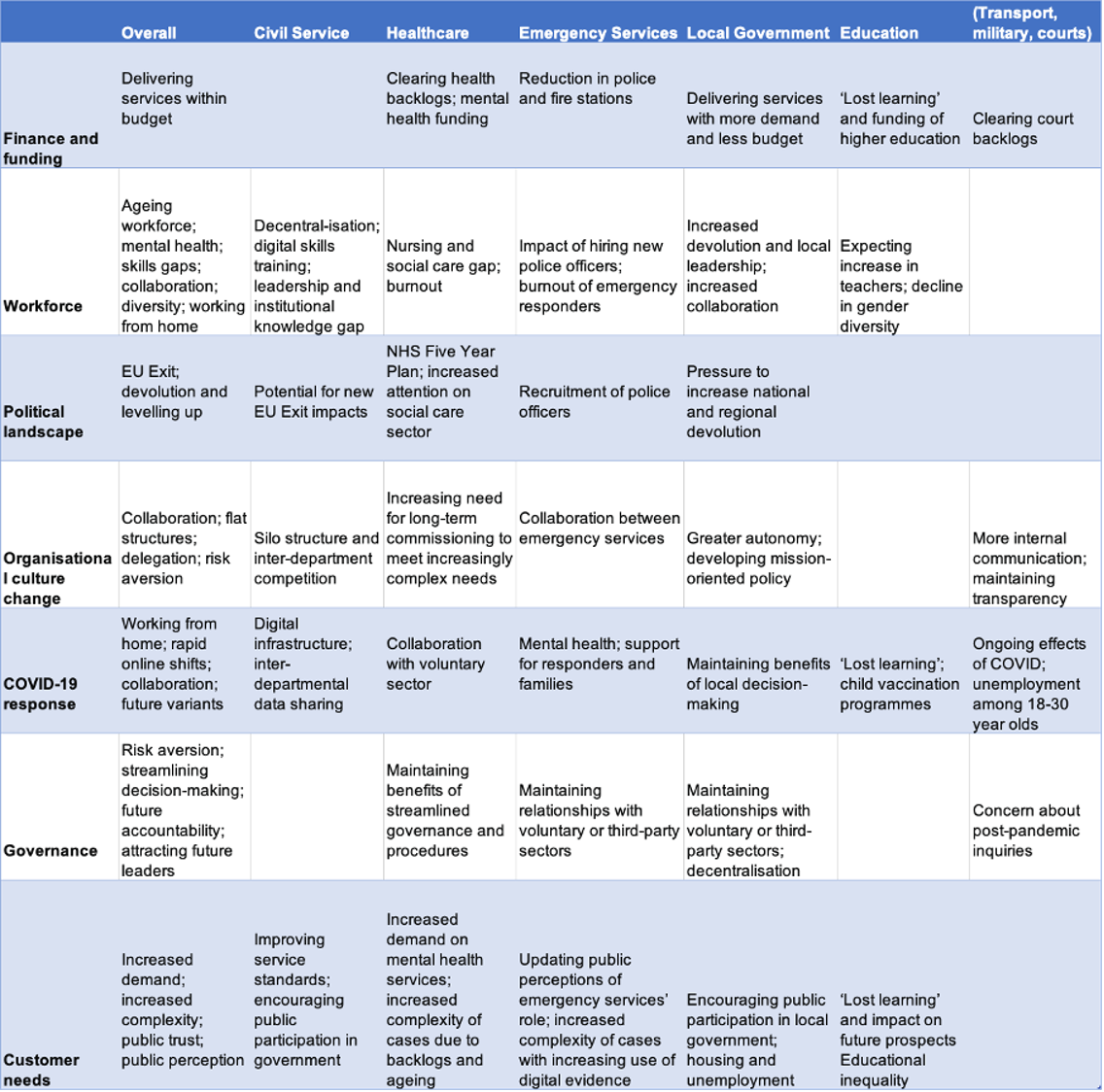
For further details of the key challenges facing public service leaders by sector (Civil Service, Healthcare, Emergency Services, Local Government, Education, Transport, Military, Courts), please see the table in Appendix 1.
Major Risks
In the context of the above sector pressures, two key, high-scoring areas of risk emerge from numerous public sector and local authority risk registers:
Risk of Service Disruption
Risk
The UK public sector and local authorities are facing increased challenges to their ability to provide core services and to collaborate effectively with partner organisations in the face of emergencies. The need to respond to, and recover from, service disruption is increasingly important given the increase of threats from:
- National and international security incidents
- Climate change and severe weather incidents
- Cyber attacks
- Continued uncertainty over the implications of the UK’s relationship with the EU
Consequences
The reported consequences of these risks include:
- Serious threat to the delivery of critical public services
- Increased financial costs from recovery and insurance costs
Typical Risk Controls (RCs)
- (RC 1) Ongoing programme of review relating to ICT Disaster Recovery and Business Continuity arrangements.
- (RC 2) ICT resilience improvements are embedded as part of the ICT Transformation Programme.
- (RC 3) Business Continuity Management Policy and overarching Business Continuity Plan in place, underpinned by business continuity plans at service level.
- (RC 4) Offsite emergency plan and regular exercises to validate the effectiveness.
Risk of Protecting Personal and Sensitive Data whilst Moving Public Services Online
Risk
With central and local government undergoing rapid digital transformation, and typically moving public services online, the obligations to protect personal and sensitive data relating to staff, service users and citizens are becoming increasingly challenging. This move towards cloud-based services is compounded by the shift to remote/flexible working and the necessity for resilient and secure IT systems.
With malicious attempts to gain access to secure digital environments becoming more sophisticated, the potential damage also increases. This risk is further exacerbated by the human factor placing limitations on what people can reasonably be expected to do to uphold the security of the organisation.
Consequences
The reported consequences of these risks include:
- Data Protection breach and consequent Information Commissioner’s Office (ICO) sanction
- Damages claims
- Reputational damage
- Potential significant business interruption if systems require shutdown until magnitude of issue is investigated
- Loss or corruption of data
- Loss of key systems; potentially impacting the ability to deliver statutory services
- Partners unable to discharge their duties
- Complaints
Typical Risk Controls (RCs)
- (RC 5) Staff are required to abide by IT policies that set out the required behaviour in the use of the technology provided. These policies are reviewed on an annual basis for appropriateness.
- (RC 6) Further training introduced relating to cybercrime, cyber security, and social engineering to raise staff awareness and knowledge.
- (RC 7) External reviews of the Authority's security compliance are carried out to maintain accreditation and confirm best practice is applied
Leveraging Technology to Enable the Risk Control
In reviewing each of the Risk Control actions, it is possible to understand how technology, such as an Identity Management system, can extensively support the delivery of the risk control actions and the detail of how this is achieved is as follows:
| Risk Control No. | Control | How an Identity Management enables the Control |
| 1 | Ongoing programme of review relating to ICT Disaster Recovery and Business Continuity arrangements. | Using a cloud-based identity management solution can provide a ‘DR proof’ method of enabling user to continue to access web applications and services without reliance on core ICT infrastructure should this be unavailable in a disaster. |
| 2 | ICT resilience improvements are embedded as part of ICT transformation programmes. | Typically, ICT Transformation Programmes are migrating services online and to the cloud therefore adopting a cloud-based identity management solution will deliver embedded resilience. |
| 3 | Business Continuity Management Policy and overarching Business Continuity Plan in place, underpinned by business continuity plans at service level | As above. |
| 4 |
Offsite emergency plan and regular exercises to validate the effectiveness. |
Cloud-based identity management or Identity as a Service (IDaaS) can be easily adopted and tested as part of regular business continuity and emergency planning. Users can test that access to the identity management solution and other cloud applications is easily available from outside the corporate network in an emergency scenario with the additional protection of Multi-Factor Authentication. |
| 5 | Staff are required to abide by IT policies that set out the required behaviour of staff in the use of the technology provided. These policies are reviewed on an annual basis for appropriateness. |
A good identity management solution can ensure that the most critical and secure IT policies are enforced by a system rather than leaving this action dependent staff manually complying with policies. One example of a policy that can be automated is in the detection and management of “Shadow-IT” risks where users may be storing corporate data in “unapproved” applications that are not secure. Another example of a policy being addressed by technology, would be security policy requirements that mandate users create strong passwords for 3rd party applications – a good identity management solution can automate password policy enforcement by updating passwords on 3rd party applications removing the burden from users and eliminating the risk of relatively weak passwords being used. |
| 6 | Continued training* introduced relating to cybercrime, cyber security and social engineering to raise staff awareness and knowledge. |
The need for training relating to cybercrime, cyber security and social engineering can be almost eliminated by using technology to eliminate the key risk areas. It can also address the broader cybercrime and cyber security risks associated with user passwords and “Shadow-IT”. |
| 7 | External reviews of security compliance are carried out to maintain accreditation and confirm best practice is applied | Effective identity management systems can provide governance and control over access to systems and data, satisfying an extensive range of compliance obligations (i.e. ISO 27001, Cyber Essentials Plus, etc) with one system. |
* Risk Control No. 6: Training – My1Login conducted a survey of 1,000 business leaders and 1,000 employees to understand the impact of Cyber Security training on employee behaviours. This study identified that Cyber Security training had an almost negligible impact on employees adopting more secure practices.
Summary
An effective identity management solution can directly mitigate some of the key threats currently facing the public sector and local authorities by addressing a number of the typical risk control actions head-on.
Identity management is used in this context as a catch-all term that encompasses services such as Identity and Access Management (IAM), Identity as a Service (IDaaS), Single Sign-On (SSO), Passwordless, Multi-Factor Authentication and Enterprise Password Management. Some vendors, such as My1Login, can provide all of these services within one solution, significantly increasing return on investment.
With an effective Identity and Access Management solution, public sector and local authority organisations can take a system-driven approach to the control actions that mitigate the above key risks rather than depend on training and the human factor.
In addition, a solution such as My1Login, can directly alleviate a number of the current pressures reported across the public sector as follows:
- Budgetary Pressure: My1Login provides management information on the actual use of software across the organisation enabling direct cost-savings as a result of cancelling dormant subscriptions and licences. Use of Single Sign-On improves workforce productivity by eliminating time wasted logging into services and provides efficiencies across IT and Service Desk functions as a result of fewer password management issues. Passwords are also cited as the root cause of over 80% of data breaches and My1Login’s Identity and Access Management solution can vastly reduce this widespread attack surface and eliminate password phishing risks.
- Workforce Management: My1Login’s SSO can be used to remove the burden of password management from users, eliminating the associated risks and using a system to manage identities. This enables frictionless access to systems for employees, and eliminates password fatigue and frustration, enabling employees to focus on delivery of public services.
- Covid-19 Response: My1Login enables public sector employees to benefit from seamless, remote access to public sector cloud applications and services with the additional security of Multi-Factor Authentication where required supporting rapid switching to remote working where required. My1Login’s Enterprise Password Manager helps support public sector organisations in managing the transition to online services by providing a mechanism to secure user and administrator access to cloud-based services mitigating the financial and reputational damage of a data breach.
Find out more about how My1Login can help address public sector and local authority risks.
Appendix 1
From the GCSU report, the key pressures facing public leaders by sector are as outlined below.