
Identity and Access Management: What Matters Most When it Comes to ROI?
This blog examines the profound impact that User Experience and Application Compatibility can have on the business case and return on investment (ROI) delivered from Identity and Access Management (IAM) products and services. This blog specifically focuses on the impact on Single Sign-On (SSO), Enterprise Password Management, Passwordless and Identity as a Service (IDaaS) solutions.
Each of these technologies holds unique value for organisations, but there are some common factors that must be considered when evaluating their use in your environment and there are a number of key factors that need to be considered in the return on investment appraisal for any business case.
Introduction
The identity and access management market has been growing rapidly over the last few years, particularly in its ability to offer single sign-on, password management and identity as a service. Overall user security is often the main driver for companies evaluating IAM products, but another key driver is compliance with ever-changing regulations such as PCI DSS, HIPAA, GDPR and NIST/NCSC.
Business cases for IAM solutions will typically include assessing the following areas:-
- Security - how effectively does the solution mitigate risks?
- Productivity - how does the solution improve productivity and in what areas across the enterprise?
- Compliance - how effectively will this mitigate current and potential future compliance
obligations? - Efficiency - What are the use-cases that will be addressed delivering efficiencies across the user base?
- Cost Reduction - In what ways will the solution reduce our cost base?
However, there are two key factors that fundamentally influence all these business case benefits; User Experience and Compatibility, and this paper illustrates the hidden pitfalls to be aware of when reviewing your IAM requirements and what you can do to improve ROI.
Understanding the Threat Landscape
Shadow-IT
Usernames and passwords (i.e. credentials) are cited to be responsible for over 80% of hacking related breaches and given this it’s no surprise that one of the most common drivers for IAM solutions is security. Most enterprises still use the corporate directory as a gateway to authenticate users either on-prem or over a VPN (Virtual Private Networks). Enterprise security at this external permitter of the network is often relatively strong. Most organisations would argue they have Single Sign-On because they’re able to daisy chain the trust at the perimeter of the network and use it to permit user SSO access to other corporate applications once authenticated and/or trusted. This works well for most enterprises and is typical when using Active Directory, Azure or an Azure AD hybrid directory structure and it provides a secure, Passwordless authentication process for users accessing the small handful of core applications that are a common denominator across the organisation.
Great, problem solved! Or is it? Some surveys have reported that enterprise users have, on average, 27 different username and password combinations required for various applications. So, why the disparity with the small handful that IT have configured with SSO? Enter, “Shadow-IT”. The use of cloud applications within enterprises and volume of sensitive corporate data being stored in the cloud is increasing exponentially. Often, the decisions on which applications to adopt are being made outside of the IT function, by the departments, or due to the need to collaborate with other organisations.
As a result, the enterprise attack surface is increasing rapidly with volumes of corporate data protected by nothing more than an email address and relatively simple password created by the user.
So the real risk vector here is not the applications that have already been integrated with SSO, it is the very large, residual risk of any single one of the many “unknown” cloud applications being compromised and this risk is far higher than the risk to core corporate applications as they will most likely be protected by a relatively simple password.
Cloud Apps that Don’t Integrate with SSO
Next we have the large set of public and private cloud applications that don’t have connectors available for SSO (i.e. using SAML or OIDC) and still require passwords for protection. Again, these apps may not be used widely across the organisation but they often hold critical, sensitive or personal data that if compromised could have very serious consequences. One example might be a password protected CRM app being brute forced, or someone hacking into your company’s account in the US Securities and Exchange Commission, or Companies House website in the UK to hijack your organisation – it has happened and often the treasury department or company secretarial function responsible for managing, and potentially sharing, the passwords that protect these accounts will be unaware of the risks.
Legacy Windows Desktop Applications and “Thin-client” Apps
Applications that run as a Windows executable file, either full blown desktop applications or more often these days, windows executables that launch thin-clients will typically not integrate with most SSO solutions. This further increases the threat surface are since these apps too will require passwords to be managed by users and not by a system, leading to insecure practices that create data breach risks for the enterprise.
Apps integrated with SSO vs other cloud, windows desktop and Shadow IT apps.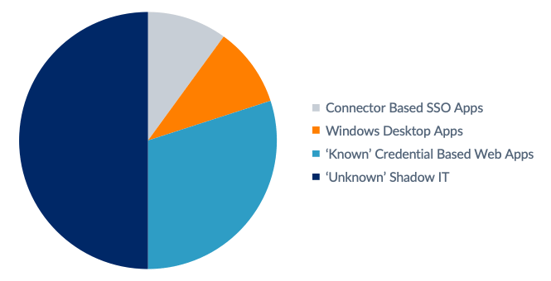
IAM Solutions
Looking at this through the optic of solutions there are a few, key products that can help:-
Single Sign-On
Single Sign-On solutions typically require users to authenticate with them in some way, or log in to a portal, then click icons that launch applications using passwordless protocols such as SAML or OIDC to onward authenticate the user with their applications. This entry-level SSO works with applications that use these protocols but leave sizeable gaps in the threat landscape by failing to cover the broad range of applications typically in use across the enterprise.
Some solutions also perform SSO using password “vaulting and forwarding”. From the user’s perspective, this provides SSO for applications that don’t natively support authentication protocols i.e. they only support credential-based logins with usernames and passwords. Again, the user experience is such that the user typically must manually log into the SSO solution first then launch the desired application from their portal. This can provide integration with a wider range of applications but can potentially fail to integrate desktop executable apps and fail to discover “Shadow-IT” applications. When you are considering SSO, make sure your solution can discover Shadow-IT apps and enable these to be easily integrated with SSO where desired. Also use a solution that has the broadest range of app compatibility (i.e. potentially able to integrate with apps that present as Windows desktop or virtualised, thin-client apps).
These SSO solutions often require the user to manually authenticate with the SSO solution first and navigate to apps via portal which creates barriers to adoption and usage. Instead use a SSO solution that can be configured to run seamlessly in the background so the users don’t have to know about it or be trained on it – they just launch an application and get signed in – which will guarantee usage, vastly improving the true ROI for your enterprise.
Enterprise Password Management
Enterprise Password Management provides enterprises with more advanced functionality in relation to applications that require passwords. On one level, an enterprise password manager can, where you have permitted, enable users or a subset of users to share specific credentials – so for example the procurement team might have access to multiple online procurement portals with various vendors and access to each of these might be via a single password for your organisation. Whilst this is relatively pedestrian functionality for an Enterprise Password Manager there are additional features you should look for that form part of your ROI evaluation.
Some Enterprise Password Managers can enforce password policies on 3rd party web applications. In other words, the enterprise administrators can configure, centralised, application specific policies and the Enterprise Password Manager can automatically generate a long, random, high-entropy password in line with the policy and set this password on the 3rd party web application without the need for an API. A good Enterprise Password Management solution should be able to take this one-step further and enable the newly generated and updated password to be hidden from the user, meaning they don’t know it, and if they don’t know the password, how can they be phished for it?
Identity as a Service (IDaaS)
Single Sign-On solutions and Enterprise Password Managers are typically available as cloud-based IDaaS services rather than on-premises based solutions.
If you are using an IDaaS service one paramount question to ask is “Does the vendor have any access to the encryption keys that protect your data?”. Some of the world’s largest vendors are designed in such a way that they have access to the customer’s encryption keys and can therefore access their customer’s data i.e. passwords. This creates a significant vulnerability in the enterprise security which can undermine the security aspect of your return on investment. Make sure you select an IDaaS vendor that does not have access to your encryption keys, and therefore data.
Objectively Measuring the Security ROI From Different IAM Solutions
Let’s analyse how the ROI might stack up across different solutions primarily in the context of delivering the intended security benefits. Looking at the business case for IAM from this perspective will also have parallels with the enterprise’s ability to meet the broader objectives so this is a useful optic on ROI.
Single Sign-On Compatibility with Application Types
First let us consider how compatible each solution is with several types of applications. So, in the interests of simplicity let us use a scale of compatibility from 1 to 5, where:-
|
Criteria |
Compatibility Score (out of 5) |
|
SSO is compatible with most of the core enterprise apps we use (using protocols i.e. SAML and OIDC) |
1 |
|
SSO is compatible with most of the core enterprise apps we use (using protocols i.e. SAML and OIDC) and is compatible with many of the web applications that use passwords |
3 |
|
SSO is compatible with most of the core enterprise apps we use (using protocols i.e. SAML and OIDC) and is compatible with almost all of the web applications and Windows desktop applications that use passwords |
5 |
Single Sign-On User Experience (UX)
|
Criteria |
UX Score (out of 5) |
|
The user must navigate to a Single Sign-On portal, product or app then sign in to start using SSO and the applications have to be launched from the portal |
1 |
|
The user must navigate to a Single Sign-On portal and launch their applications from the portal |
3 |
|
The user does not have to navigate to or sign into a portal – they just launch their applications as intended and the Single Sign-On solution works automatically |
5 |
Extent to which User’s Adopt the Solution for Corporate Apps
|
Criteria |
Adoption Score (out of 5) |
|
The users decide whether to manually configure the SSO or Enterprise Password Manager for use with their corporate applications |
1 |
|
SSO and the Enterprise Password Manager are configured to work for the small handful of core applications in use across the business, but it is up to the user whether they use it for the wider range of corporate applications |
3 |
|
The solution detects all applications (i.e. Shadow-IT) being used by users and enables the administrators to activate policies that automatically invoke Single Sign-On for all relevant corporate applications without the user having to take any action |
5 |
Profiling the Risk, Effectiveness and ROI
The scores above are compound since the extent to which the solution is compatible with apps impacts the extent to which the user experience is relevant and these impact the extent to which applications are adopted, so for maximum risk mitigation we would expect a maximum solution effectiveness and ROI score of:
Compatibility (5) x UX (5) x Adoption (5) = Maximum solution effectiveness and ROI of (125)
Now let us take two real world product scenarios and measure them against the criteria:
IAM Product 1:
Compatibility: SSO works with protocols and connectors (3)
UX: The user has to sign into a portal to use the SSO product (1)
Adoption: Core apps are already configured but user decides whether to add other apps (3)
IAM Product 2:
Compatibility: SSO works with all app types (5)
UX: The user just launches apps as per usual - no change in behaviours (5)
Adoption: Adoption across all relevant apps can be mandated by administrators (5)
So based on our criteria above:
| Solution | Compatibility | UX | Adoption | Effectiveness Score |
| IAM Product 1 | 3 | 1 | 3 | 9 out of 125 (7%) |
| IAM Product 2 | 5 | 5 | 5 | 125 out of 125 (100%) |
Summing up the risks
Clearly the above is not definitive and you might wish to adjust the criteria to suit your own methods of measuring effectiveness but what this does illustrate is that User Experience and Compatibility of your chosen SSO solution could have a fundamentally profound effect on your genuine return on investment compared to your business case, increasing the risk of financial and reputational damage from a data breach.
Here are a Few Takeaway Actions with Considering
- When evaluating IAM solutions – particularly Single Sign-On or IDaaS, choose a solution that can integrate Single Sign-On for the broadest range of applications. That way you are less likely to have application ‘blind-spots’ and you are future-proofing your IAM investment.
- Review the User Experience of any Single Sign-On or Enterprise Password Manager – does it work in the background with no or minimal user intervention or does it create additional barriers to users accessing the application they are really trying to get to.
- The core apps your enterprise have covered with any existing Single Sign-On solution are typically not where the risk resides. The greater risk is now hidden within the apps you have not integrated with an identity management system or do not even know about yet. So when evaluating Single Sign-On solutions opt for one that discover “Shadow-IT” apps and allow administrators to integrate these with the flick of a switch meaning that users cannot circumvent the use of the product.
- There are some IDaaS solutions that comprehensively cover a combined offering for Single Sign-On and Enterprise Password Management. This can deliver increased cost efficiencies as a result of only purchasing one solution, delivering an improved ROI from your IAM investment, particularly in the context of the points discussed above.
Related Articles
Five mistakes businesses make which cause data breaches
The frequency and severity of data breaches are continuing to grow, with the cost of the average breach rising again in 2021 to over £3 million. The previous year,...The Enterprise Risks of Personal Password Managers
With the average enterprise organisation using 288 different cloud applications, individual users simply have too many credentials to remember, and resort to poor...Identity and Access Management for Web, Mobile and Windows Desktop Applications
Identity and Access Management for Web, Mobile and Windows Desktop Applications










-
© My1Login 2007 - 2026
- Terms & Conditions
- Anti-Slavery Policy
- Back to the top ↑
