Single Sign-On (SSO) authentication processes allow users to authenticate once and gain access to multiple applications or systems without the need to re-enter credentials (such as usernames and passwords) for each application. SSO has major benefits for cyber-security conscious organisations, such as enhanced security, boosting productivity, and releasing cost savings.
Protect your business against security breaches, enable secure remote working, prevent credential-phishing and make a move towards passwordless authentication with My1Login’s Identity and Access Management and Single Sign-On Solution.
Advanced Single Sign-On solutions such as My1Login include the ability to:-
- Run in the background with Zero Login so workforce adoption is guaranteed
- Perform SSO that includes automatic entry of One Time Passwords on external applications
- Automate password policy enforcement on external applications where passwords are required
- Provide integrated, advanced password management
- Enable Single Sign-On for web and Windows desktop apps
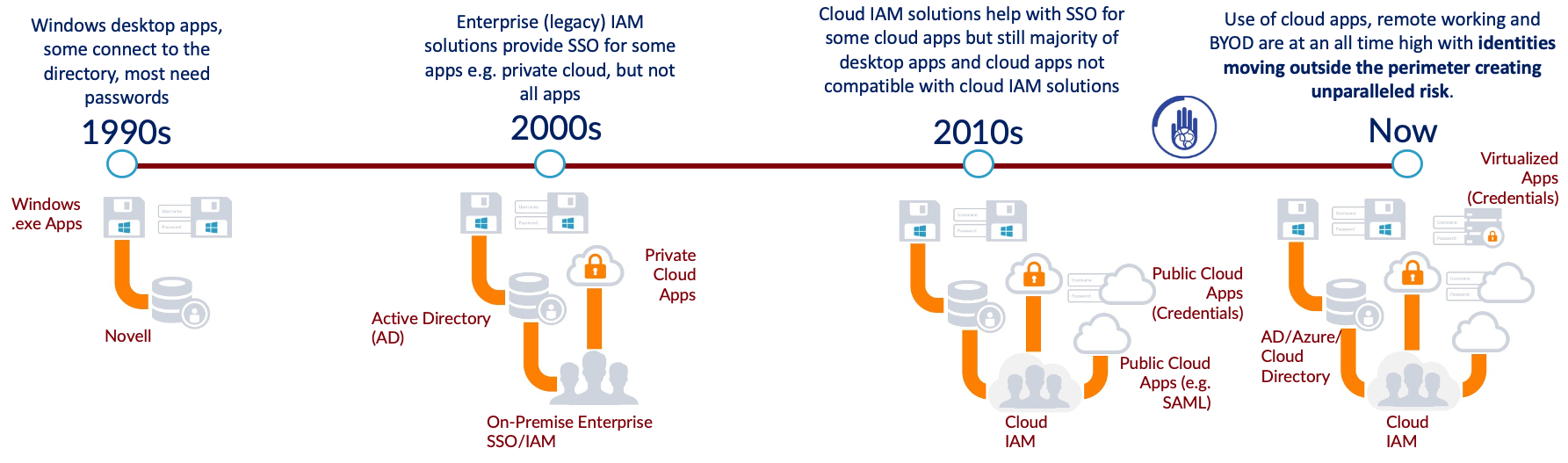
History of SSO
The first Single Sign-On solutions appeared with Active Directory in the late 90s, an early Access Management system that was first launched with Windows 2000 Server Edition. Active Directory was designed with the typical office environment of the time in mind – almost entirely Windows devices using on-premises resources.
Over the next decade, there was a migration towards using internal, private web applications. Often referred to at the time as “intranet applications”, this increased the amount of login credentials required by the workforce and some early, on-premise Single Sign-On solutions emerged to address this. These early solutions were fairly restrictive in that they were on-premise, and typically only integrated with other, on-premise apps. They served their purpose for a while and became deeply embedded in the foundations of enterprise. However, as organisations began to adopt public cloud applications, these legacy on-premise SSO solutions became restrictive and inflexible, failing to meet the needs of the workforce.
At this point, cloud-based Single Sign-On providers began to emerge, providing flexible, scalable SSO in the cloud that was purpose built for integrating with the growing number of Software as a Service (SaaS) applications being adopted by enterprises. Today, the migration towards the cloud has continued to progress. With remote working, use of mobile devices, Bring-Your-Own-Device policies, and the increasing prevalence of cyberattacks necessitating more comprehensive solutions. Now, an effective SSO solution must deal with identities across multiple devices and operating systems while providing access to internal and external cloud apps, as well as virtualised apps, legacy apps and some that still present as Windows desktop executable applications.
The Evolution of Authentication
How does Single Sign-On work?
My1Login’s Single Sign-On (SSO) solution works by enabling users to authenticate once with the corporate directory (e.g. Entra ID, Active Directory), and then gain access to multiple applications, services, or systems without having to log in again for each individual resource. Users do not have to manually authenticate with My1Login if they are already authenticated with the corporate directory. My1Login takes the trust delegated by the corporate directory and uses this to provide onward, Single Sign-On authentication to internal web, external cloud and Windows desktop applications. This SSO is supported using identity protocols (e.g. SAML and OIDC), or using credentials (e.g. usernames and passwords).
How Single Sign-On Works:
- When a user attempts to access an application, the application recognises that the user is not yet authenticated.
- If the application requires credentials for authentication and the user is already authenticated with My1Login, then My1Login will provide the relevant credentials and automatically trigger the sign in process. My1Login can also automate the generation and entry of One Time Passcodes (OTPs) for the user if required.
- If the application uses an identity protocol such as SAML or OIDC:
- the application redirects the user to My1Login’s SSO platform for authentication. If the user is already authenticated with My1Login (e.g. as a result of having already authenticated with the corporate directory) then My1Login generates a secure token.
- This token contains information about the user's identity and authentication status.
- My1Login sends the generated token back to the application that initially requested authentication for the user.
- The application verifies the token's authenticity and the user's identity and permissions within the token.
- The user is now authenticated and gains access to the application without needing to enter credentials.
This entire process happens within a matter of seconds, enabling fast and secure access to the applications your workforce need to use.
SSO vendors - IdPs and IDaaS
With SSO solutions, the process of authenticating users is carried out by a third-party Identity Provider (IdP), often the vendor of an SSO solution. Where these Identity and Access Management solutions are cloud-based, this is typically referred to as Identity-as-a-Service, or IdaaS. A relationship of trust exists between the user and the IdP, and the IdP and the providers of applications (Service Providers, or SPs). When these three entities can communicate securely with one another, this allows one identity to be used to access multiple systems. Instead of the user being authenticated by the SP after entering in a username and password, a request is sent to the IdP when the app is accessed. The IdP then confirms the user’s identity to the SP, which then authorises them to access the service.
Token-based SSO Authentication
The end result of the three-way communication between user, IdP and SP can be a relatively simple process:
- The user then requests access to a service provider, such as by launching a cloud app.
- The cloud app identifies the user and sends an authentication request to the IdP.
- If the user has not already identified themselves with the IdP, for instance during a previous session, the IdP will authenticate them e.g. using a password, physical device, biometrics etc.
- The IdP provides a security token to the service provider via the web browser enabling the service provider to validate the user and permitting them appropriate access based on their identity.

While this process can sound complex, the actual user experience is far simpler and smoother than a password-based system. From the perspective of an employee within an enterprise using a passwordless system, they are simply able to launch and close apps at will, without having to enter any credentials once they have authenticated with their corporate directory (e.g. Active Directory, Entra ID).
Token-based authentication relies on the use of open security standards to securely communicate between the IdP and SP, usually either SAML or OIDC. There are small differences in terminology, formatting and use cases, but the fundamental process is the same for both.
SAML and OIDC have slightly different use cases. As the more lightweight protocol, which is easily deployed at internet scale where large numbers of claims can be processed quickly, OIDC is usually preferred for authenticating users on mobile apps, landing pages and consumer-facing environments. In contrast, SAML is more frequently used in enterprise authentication due to its maturity, reliability and relatively widespread compatibility. Most IdPs will support the use of both, although individual SPs may often use only one or the other. Whilst OIDC and SAML protocols are supported as standard by the largest, and most commonly used enterprise apps, the vast majority of line-of-business applications used across the enterprise do not support these protocols and still rely on passwords for authentication.
SSO Authentication for Web Apps (Using Passwords)
The overwhelming majority of cloud apps and legacy desktop apps that are used by the enterprise workforce are not compatible with SAML or OIDC, meaning they still rely on passwords for authentication. Some IdPs however, can provide a Passwordless experience for these applications, by automating the authentication of the user using a built in enterprise password manager to store the credentials and release these to the appropriate application, providing SSO at the point the user requires this.
Solutions that provide this combined SSO and enterprise password management capability can also be used for password policy enforcement by automating the generation of random, complex passwords and updating these in the external applications.
From the user’s point of view, the SSO process is almost identical to token-based SSO – the user launches or navigates to an application and, assuming they are already authenticated with the corporate directory, are automatically signed into the application by the SSO solution. The SSO solution should also be able to hide the application password from the user meaning they are not required to remember or manage this. Since this password can be hidden from the user, and they are not required to create, manage or enter passwords, it provides many of the same security benefits as token-based authentication, such as protecting against phishing or credential-stuffing attacks.
SSO Authentication for Windows Desktop Apps (Using Passwords)
Across the enterprise workforce, there are often numerous, line-of-business, Windows desktop applications in use. Whilst not necessarily core applications, these are often heavily relied upon within specific departments. They can range from legacy, Win 32 style, applications to modern, thin-client applications that are launched as desktop executables then open up some sort of web-based interface. Typically, the authentication for these apps does not readily integrate with the corporate directory e.g. Entra and, as a result, they can present a significant security risk in addition to being a source of user friction.
A good SSO solution should also be able to provide Single Sign-On for these Windows desktop applications, without needing to use identity protocols. The SSO solution should recognise the Windows desktop application being launched, then automatically submit the user credentials when prompted, providing a seamless experience for the user that removes the need for them to manage passwords.
IdP-initiated vs SP-initiated SSO
The process of initiating the authentication process for SSO can be carried out in one of two ways – IdP-initiated and SP-initiated.
For IdP-initiated SSO, the user typically accesses a portal provided by the IdP. This will contain links to all apps that are part of the SSO system, and the user must launch the apps from here in order for the SSO process to be triggered. Once the relevant app link has been clicked, the application will be launched, making an assertion to the SP application, the SP will validate this and authorise the user to use the service.
In SP-initiated SSO, the user simply navigates to the SP app through their browser, and the app delegates the authentication of the user to the IdP. If the user is already authenticated with the IdP then the process is typically invisible to the user experience. This has the advantage of not requiring a change in user behaviour, helping maximise adoption rates and negating the need for additional training.
Federated Identities vs Enterprise SSO vs Single Sign-In
These forms of IdP and SP initiated SSO are examples of Federated Identities, in that they allow a single identity to be linked across multiple identity management systems with a mutual relationship of trust. This can be directly between two enterprises, or users may be given a choice of one of many identities, or there may be IdP chaining, where one identity is used to authenticate the user into a service, which is in turn used to authenticate them to a third service. This is most commonly seen in consumer-facing apps, particularly with social media identities – for example, Spotify may allow users to authenticate using their Facebook or Google accounts.
For many organisations, there is still a reliance on legacy, Enterprise Single Sign-On solutions, these on-premise solutions were common in the 2000s and typically enabled integration of a small number of core, “intranet” applications with SSO. SSO for a wider range of enterprise Windows desktop applications was often provided by utilising password synchronisation products. These products synchronised the usernames and passwords of numerous, stand alone identity databases for various applications with the user’s Active Directory username and password. This enabled users to access these applications using their Active Directory credentials and is often considered more of a Single Sign-In solution rather than Single Sign-On solution. The most effective identity solutions are those with the broadest range of compatibility with multiple application types, including:
- Windows Desktop
- External Web/Cloud
- Internal Web/Cloud
- Mobile
- Virtualised
SSO and IdaaS solutions that leverage the enterprise’s corporate directory for the initial verification of users provide a much greater return on investment since the barriers to usage and adoption are greatly reduced compared to identity solutions that require the user to manually authenticate with them. The more seamless the experience for users and the more comprehensive the compatibility with various types of applications used by a workforce, the more benefits there are for the enterprise.
What are the benefits and business case for SSO?
Cyber Security Benefits of SSO
Cybersecurity challenges are the main drivers for enterprises moving towards modern, high-impact SSO solutions. With the average enterprise using 288 different cloud applications, requiring the workforce to memorise separate passwords for each app is no longer feasible. Without an SSO solution, users often resort to poor security practices such as using weak or reused passwords, which serves to compound the impact of a data breach if credentials are compromised.
Modern, high-impact SSO solutions tackle the inherent security issues of passwords by taking the responsibility of managing credentials and identities away from the user and putting the organisation back in control of identities, preventing many types of attack that can leverage weak security practices and human error.
Extent of Cyber Risk Mitigation
The largest, and arguably most important, factor in delivering the cyber security benefits of a Single Sign-On solution is the extent to which it mitigates cyber security risks. This level of risk mitigation, and therefore benefit, is driven by three key factors:
- The extent to which the SSO solution can integrate with different types of applications i.e. web, Windows desktop, virtualised etc. In other words the range of compatibility with various line-of-business apps in use across the enterprise.
- The ability of the SSO solution to work in the background, without users being required to engage with it, so user adoption is guaranteed.
- The ability of the SSO solution to discover Shadow-IT and line-of-business apps then integrate these with SSO.
Elimination of Phishing Risks
Another significant benefit that enterprises can realise with a modern, high-impact SSO solution is the elimination of phishing risks. A modern SSO solution will enable administrators to centrally configure strong password policies for external applications, automatically update the user passwords for these applications, then hide the new password from the user on the SSO system. The user can still use the identity to SSO into the application but is unaware of the password. The SSO solution will not divulge credentials to a spoofed URL and if the user does not know the password, it cannot be phished from them.
Cost Saving Benefits of SSO
Modern, high impact solutions can also directly release cost savings for enterprises by enabling a reduction in software license pool costs and subscriptions. If the solution is effective at integrating all types of applications, including:
- password-based,
- cloud/SaaS
- Windows desktop
- on-premise custom apps
then you will be able to derive accurate Management Information (MI) that provides a centralised audit trail of the extent to which various applications are being used across the organisation within a defined period. This actual usage can be reconciled against the number of subscriptions or licenses the enterprise is paying for on each of these applications to identify opportunities for cost savings from redundant licenses and subscriptions.
Efficiency and Productivity Benefits of SSO
In addition to direct cost-savings, modern, high-impact SSO solutions can also deliver a range of productivity and efficiency benefits to enterprises as a result of:
- Increasing end user productivity by eliminating downtime associated with forgotten passwords and time wasted manually logging in to apps
- Minimising Service Desk administration associated with password related incidents
- Reducing IT and departmental onboarding and offboarding costs by automating user account lifecycle management
Reducing User Friction
Another major benefit of SSO solutions is the vastly improved user experience, particularly when the SSO solution is capable of working with all corporate applications. If you don’t have applications covered with SSO then users will be left creating and managing their own passwords for these applications. When they need to log in, they have to navigate to the application, find the correct username, type or copy and paste this into the username field, then type or copy and paste the password into the password field. This can be 7 or 8 steps in total, most of which can be eliminated with a SSO solution that enables navigating to the app and logging in with a single click.
Compliance Benefits of SSO
Modern, high-impact SSO solutions can also provide enterprises with a vast range of compliance benefits. Given the SSO systems can be used to:
- control user account lifecycles
- enable management and governance of identities and access to data
- provide full, centralised audit trails of user access to applications
- envoke step-up and Multi-Factor Authentication for SSO into specific apps
This can be used to satisfy audit and compliance obligations that underpin a wide range of local and global compliance frameworks and standards.
For more information on building the business case for Single Sign-On see here.
Why is SSO more secure?
SSO is fundamentally more secure than not having SSO in place because it significantly improves an organisation’s security posture in mitigating the risk of data breaches.
With a Single Sign-On solution, the initial authentication takes place either with the user verifying themselves directly to the IdP, or via the enterprise’s existing corporate directory. While this may be perceived as a single point of failure, the reality is that the alternative – requiring users to memorise dozens of different corporate passwords – creates many points of failure which are far weaker and more difficult to secure. Using SSO to leverage the trust delegated by the corporate network ensures even cloud applications can have the same level of security as the corporate network.
Maintaining so many passwords is only possible for the typical employee by adopting unsecure practices such as writing passwords down, reusing them, or using easy-to-crack passwords. If the user is only required to authenticate themselves with a single set of credentials, additional layers of security are easily added to this, such as the requirement to be on the corporate network (either physically or through a VPN), or the addition of Multi-Factor Authentication.
The greatest risk to corporate data is unauthorised access to the cloud applications that exist outside of the network perimeter. Having an SSO solution in place enables these apps to be protected, either by:
- Leveraging passwordless authentication where supported, using identity protocols such as SAML or OIDC.
- Where passwords are required, using an SSO solution that can make these all unique, high-entropy passwords that are orders of magnitude more secure than passwords created and managed by the workforce.
Where the workforce are responsible for managing corporate password, this opens up the enterprise to the following risks:
Phishing attacks
The growth of phishing represents the biggest challenge in cybersecurity for enterprises, with Verizon’s Data Breach Report finding that phishing was the most common action in data breaches, present in 36%.
In more modern, sophisticated attacks, users are usually redirected to a login page which is a spoofed version of a site or app they may frequently log into. When their credentials are entered, the attacker can use these to gain access to their account in the future, as well as any others that reuse the same credentials.
When an organisation implements an SSO solution, however, passwords are either replaced with token-based authentication, or can be hidden from the workforce. This essentially makes a successful phishing attack impossible – in the case of token-based authentication, there is no password that can be entered into a spoofed site, and in the case of and SSO solution that can hide passwords from users, the user cannot be phished of the password since they are not aware of the passwords. In both cases, the SSO solution will also not recognise the site as trusted, so no credentials will be disclosed.
Brute force attacks
Where password-based authentication is used, brute force attacks are always an option available to hackers looking to break in. By using programs which test millions of combinations of usernames and passwords per second, these attempt to simply guess their way into any account. With the increase in hybrid working environments, these have become a particular issue since they often target Remote Desktop Protocol ports, which are required to be open for many remote working situations. By prioritising commonly-used passwords, these programs are able to exploit lax practices when employees are responsible for creating and managing credentials themselves.
With SSO, token-based authentication makes brute force attacks impossible, and even where passwords are still used, extremely strong ones can be generated which will take far longer for brute force methods to crack, allowing attacks to be detected before they cause a breach.
Credential-stuffing
With four in ten UK businesses having suffered a data breach in the past 12 months, there’s a likely risk that many enterprise accounts are already compromised, particularly where employees reuse passwords that they also use for personal accounts outside the organisation. Credential stuffing attacks use a similar method to brute force, but first attempt to use credentials that have been compromised in previous data breaches, a problem exacerbated by the reuse of passwords.
With SSO, passwords are never reused between accounts, and token-based authentication ensures that the secure tokens are only valid for each individual session, making it impossible for hackers to leverage previously compromised credentials to attack other areas of the network in future.
Using Easy to Guess Passwords
Numerous surveys have highlighted the risks of letting employees create their own passwords for corporate applications. Left to their own devices, the workforce will create passwords for corporate applications that only just satisfy the application’s password policy but make it easy for the employee to remember. Examples of this would be choosing passwords that include the name of the company they work for with a number added at the end. This will satisfy most password policies but create a huge risk for the enterprise, particularly where corporate data is being stored in external, cloud applications.
Using a modern Single Sign-On solution that handles password-based authentication for web applications, and can enforce password policies on these external applications can ensure that external passwords are long, random, high-entropy strings of characters, numerals and symbols, making it almost impossible to guess the passwords that are used by the workforce.
Password Re-use
Another significant risk vector for enterprises is where the workforce re-use the same password across multiple applications. An example of this would be where they use the same email address and password combination for all of the corporate web applications they use. Another example would be where the employee uses an email address and password for personal applications and then re-uses these credentials for corporate web applications that are storing sensitive data in the cloud.
If one of these websites or applications is breached and malicious actors gain the email addresses and passwords, then password re-use by employees creates a domino effect that will enable the attackers to compromise multiple applications used by that user and potentially compromise corporate data as a result.
Modern SSO solutions that can enforce password policies on external cloud applications mitigate this risk by enabling enterprises to ensure the passwords being used by on each external application is random and unique.
Unsecure Password Storage
Numerous studies report the average employee has to manage anything from 25 to 200 corporate related passwords. Without an effective SSO solution in place this becomes almost impossible to manage securely and often results in users storing corporate passwords in unsecure locations. This might be spreadsheets or word documents, held locally, on shared servers, or even in cloud based document sharing applications. These locations are often not secure and offer rich pickings for malicious actors, creating a vastly increased attack surface for malicious actors.
Modern SSO solutions offer the benefit of being able to mitigate this risk as they are capable of providing a solution that can provide users with access to applications using authentication protocols so no passwords are required. For applications that do require passwords, modern SSO solutions often provide some integrated Enterprise Password Management functionality that can be used to enable password-based SSO and mitigate the risk of users storing passwords in unsecure locations.
Implementing SSO
What to Look for in an SSO Provider
Not all SSO solutions are created equal. It is important to find one that best meets the individual needs and challenges faced by the business. An ideal solution should have full compatibility with the suite of apps used by the workforce, facilitate an easy transition to the new system, and include other products that complement Single Sign-On, such as Enterprise Password Management, and Multi-Factor Authentication.
Choosing a SSO with Maximum App Compatibility
Before choosing a SSO solution, one of the key factors to consider is the range of application types it is compatible with. This will be one of the most significant factors in truly addressing cyber security risks and delivering a return on investment for the enterprise. Most core enterprise applications are compatible with security protocols such as SAML and OIDC, however, many web, desktop, virtualised and legacy apps, are used extensively in line-of-business functions across the enterprise and need to be integrated with SSO to effectively address the risks. The SSO solution should therefore be able to provide password-based authentication into web, desktop and legacy applications. Ideally the SSO should be performed in such a way that the passwords are hidden from the workforce so they cannot be phished providing greater security benefits for the enterprise.
Using the Corporate Directory as the Single Source of Truth
Some IdPs and Single Sign-On solutions will use their own, standalone databases as the master repository for user identities, however others will integrate the existing corporate directory to enable user account lifecycle management and seamless user authentication. The latter option has significant benefits – as well as being easier and more rapid to deploy, individual users and groups can easily be synchronised with the existing directory, greatly reducing the time required to onboard users. In addition, if the enterprise changes IdPr in the future, thismakes it easier to switch, since the business will not be tied to a third-party directory. Leveraging directory metadata allows token-based authentication methods such as SAML and OIDC to be easily configured for applications that support these protocols. This process is only required once for each app during the setup process, and does not require extensive technical knowledge on the part of the customer.
Zero-knowledge encryption
While some Single Sign-On solutions and vendors must store passwords in order to provide SSO for applications that require credentials, , Zero-knowledge encryption ensures the vendor, or provider of the SSO solution has no access to these. This means the SSO vendor has no access to the encryption keys that protect the customer’s stored credentials. Instead the keys reside only within the secure perimeter of the customer’s enterprise network.
Ensuring user adoption
Finally, organisations need to ensure that the new SSO solution has a high adoption rate for users. The best SSO solutions can guarantee user adoption by integrating with the corporate directory to provide the workforce with SSO without having to log into, or access a portal. Solutions that can run seamlessly in the background in this way can ensure user adoption which maximises return on investment for customers.
How My1Login Enables Enterprises to Implement SSO
My1Login provides the most widely compatible Single Sign-On solution on the market due to its ability to provide SSO for:
- Web/SaaS apps using identity protocols (e.g. SAML, OIDC)
- Web apps that require credentials (i.e. usernames and passwords)
- Internal/Custom web apps
- Windows desktop executable apps
- Virtualised/Thin-client apps
- One Time Passwords
My1Login’s Single Sign-On solution can run in the background, providing the workforce with authentication into applications as they need them without users having to log into, or access, My1Login first. This ability to run in the background guarantees user adoption ensuring enterprises maximise the return on investment and security benefits of the product. Passwordless protocols can be used for SSO where supported by the applications (i.e. SAML, OIDC), with My1Login acting as an IdP to authenticate users, and password-based SSO can be provided for apps that don’t support authentication protocols. This enables a passwordless experience for applications that still rely on passwords
My1Login utilises client-side, Zero-Knowledge Encryption to protect customer’s stored credentials. With this approach, customer data is encrypted within the secure perimeter of the enterprise network before being transferred to the cloud. The encryption keys remain securely within the customer’s environment meaning even My1Login cannot access customer’s secure data. This significantly reduces the risk of a data breach.
In terms of deployment, users can be rapidly onboarded with My1Login by synchronising the existing corporate directory, enabling automated user account provisioning for users and a seamless, zero-login authentication process. This speeds up the user adoption process, reduces IT admin, and accelerates time-to-value for the enterprise.
In addition, My1Login’s zero login experience, combined with the ability to run silently in the background means that users don’t have to log in or access My1Login to use it. Users simply launch the application they wish to access and My1Login will authenticate them using SSO. This ability to run silently in the background, means no user training is required, guaranteeing user adoption and maximising the benefits and return on investment for the customer.